Learn How To Track Phones

Losing a phone in 2026 represents far more than just losing a communication device. Modern smartphones contain extensive sensitive data including financial information, personal photos, work documents, social media accounts, messaging apps like WhatsApp, Telegram, Signal, and Discord, authentication apps, and digital wallets. If your phone is stolen deliberately rather than simply misplaced, the consequences become even more serious, as malicious actors can exploit or sell your personal information on the dark web. When your device goes missing, acting quickly and methodically becomes absolutely critical to protecting yourself.
The first few hours after discovering your phone is missing are crucial. During this time window, you have the best chance of locating the device, securing your data, and preventing unauthorized access to your accounts. Understanding the proper steps to take can mean the difference between recovering your device and losing everything stored on it.
Immediate Security Measures
Before you begin the process of physically locating your device, your absolute first priority must be securing your digital assets and personal information. This is critical because a determined thief can potentially access your accounts, drain your bank accounts, steal cryptocurrency, access your email, and compromise your identity within minutes if your phone isn’t properly secured.
Immediately borrow a device from a friend, family member, or colleague and contact your bank to request a temporary block on all cards and accounts associated with your lost phone. Most banks in 2026 offer instant card freezing through their apps or 24/7 phone support. Don’t wait even a few minutes for this step because payment apps like Apple Pay, Google Pay, Samsung Pay, PayPal, Venmo, and others can be used for fraudulent transactions if someone accesses your unlocked device.
Next, using a computer or borrowed device, immediately change passwords for your most critical services. Start with your primary email account, as this often serves as the recovery method for all other accounts. Then systematically update passwords for banking apps, social media platforms including Facebook, Instagram, TikTok, Twitter, and LinkedIn, messaging services like WhatsApp, Telegram, Signal, and Discord, cloud storage services, and any other applications containing sensitive personal or financial information.
If you use a password manager like LastPass, 1Password, or Bitwarden, change that master password immediately as well. Enable two-factor authentication on all accounts that support it if you haven’t already. This adds an extra layer of security that prevents unauthorized access even if someone has your password.
Making the Decision to Block Your Number
After securing your digital assets, you face an important decision about whether to block your phone number. This decision depends heavily on the circumstances of how you lost your phone and the likelihood of recovery.
If you believe the phone was simply misplaced rather than stolen perhaps you left it at a restaurant, in a taxi, at a friend’s house, or somewhere else you can identify you might want to delay blocking the number. In these scenarios, there’s a reasonable chance that an honest person found it and would answer if you call. Many good samaritans have returned lost phones after being contacted by the owner.
Try calling your number from another phone. If someone answers and seems willing to return it, you might recover your device quickly and without complications. Offer to meet in a public place or arrange for them to drop it at a nearby police station. Some people might even expect a small reward for their honesty and effort.
However, if you have strong reasons to believe the phone was deliberately stolen from your bag, pocket, car, or home, blocking the number becomes the safer option. A thief is unlikely to return the device and leaving the number active only gives them more time to attempt to crack your security measures. Contact your mobile carrier immediately to suspend service and prevent unauthorized use of your cellular connection.
Four Proven Methods for Locating Your Phone
Once you’ve secured your accounts and made the appropriate decision about your phone number, you can focus on actually locating the missing device. There are four primary methods available in 2026, each with different requirements and success rates.
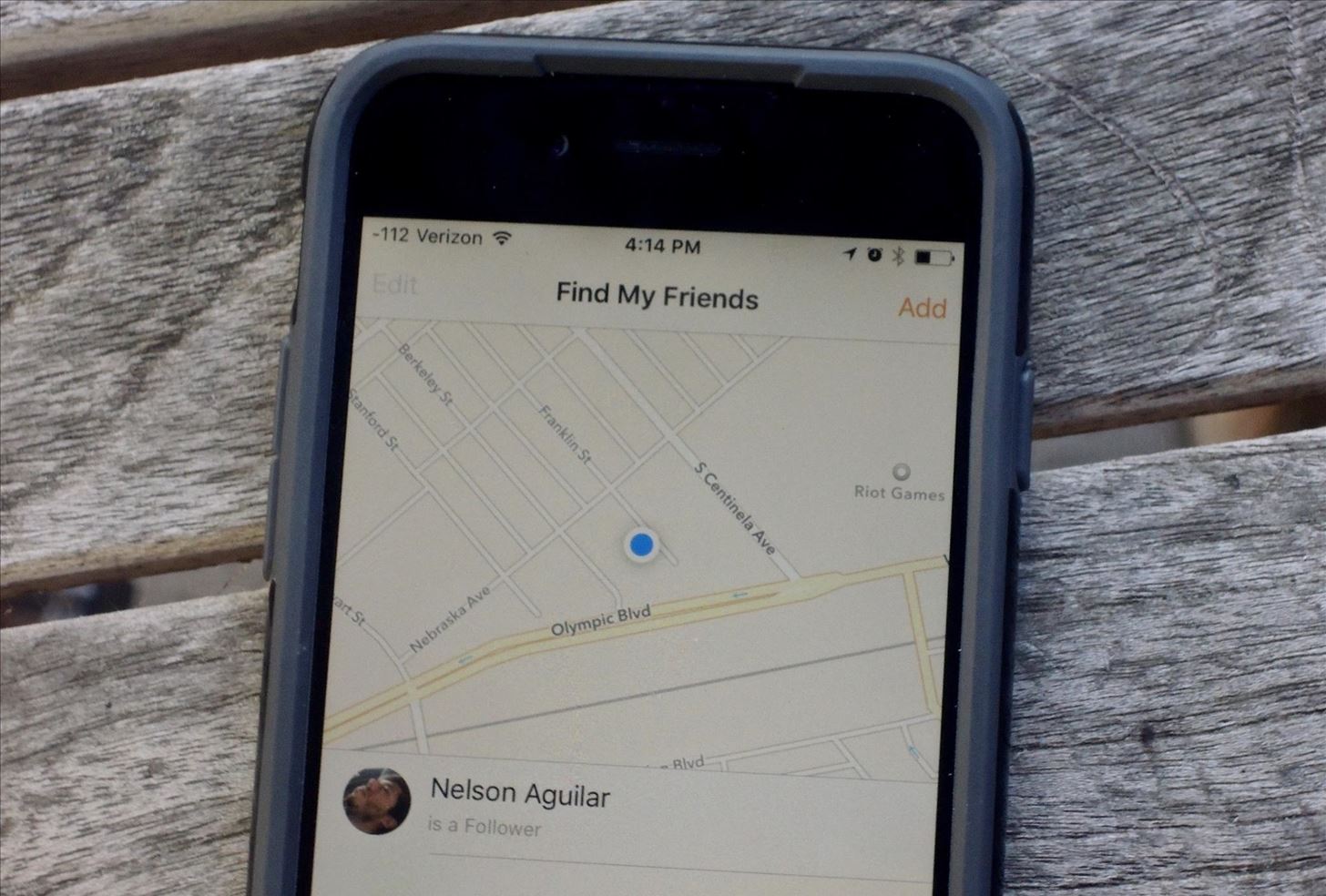
Method 1: Find My iPhone for iOS Devices
If you own an iPhone running iOS 10 or later, Apple’s “Find My” ecosystem provides one of the most robust phone recovery systems available. This method works seamlessly across all Apple devices including iPhone, iPad, Apple Watch, Mac computers, and even AirPods and AirTags.
The critical requirement is that you must have enabled Find My iPhone in your device settings before it was lost. This feature is found under Settings, your Apple ID name, Find My, Find My iPhone. If you had the foresight to activate this before losing your device, you’re in luck.
To locate your iPhone, use any other Apple device signed in with the same Apple ID and open the Find My app. Alternatively, visit iCloud.com from any web browser and sign in with your Apple ID credentials. The service will display your device’s current or last known location on a map with remarkable accuracy, often within a few meters.
Beyond simple location viewing, Find My offers several powerful actions. You can play a sound on your iPhone at maximum volume even if it’s set to silent mode, which is incredibly helpful if it’s nearby but hidden. You can enable Lost Mode, which locks the device, displays a custom message with contact information on the lock screen, and tracks its location continuously. As a last resort, you can remotely erase all data on the device to prevent anyone from accessing your personal information.
The system also shows your device’s battery level, giving you a sense of how long it will remain trackable. In 2026, Apple’s Find My network has become incredibly sophisticated, using Bluetooth signals from millions of Apple devices worldwide to locate lost items even when they’re offline.
Method 2: Google Find My Device for Android
Android users have access to Google’s Find My Device service, which offers similar functionality to Apple’s solution. This system works with any Android phone or tablet running Android 4.4 KitKat or later, which encompasses virtually all devices still in use today.
Like the iOS solution, Find My Device must be enabled before the phone is lost. You can verify this in Settings, Security, Find My Device. Most Android phones have this activated by default during initial setup, but it’s worth checking proactively on your current devices.
To locate an Android device, visit android.com/find from any web browser or download the Find My Device app on another Android phone. Sign in with the Google account associated with the lost device. The service will attempt to locate your phone using GPS, Wi-Fi networks, and cellular towers, displaying its position on Google Maps.
Google’s service allows you to ring your device at full volume for five minutes even if it’s silenced, lock it with a new password and display a recovery message on the lock screen, or erase all data remotely. The system also shows when the device was last seen and its battery level.
In 2026, Google has enhanced this service with better offline finding capabilities and integration with the broader Android ecosystem, making it easier to locate devices even when they’re not connected to the internet.
Method 3: IMEI-Based Tracking
If neither of the previous methods are available because you didn’t enable the built-in tracking features beforehand, you still have the option of IMEI-based tracking. The IMEI (International Mobile Equipment Identity) number is a unique 15-digit identifier assigned to every mobile device in the world, functioning essentially as a fingerprint for your phone.
Your IMEI number should be documented when you purchase your device. It’s typically printed on the original box, found on the purchase receipt, or can be retrieved by dialing *#06# on the phone before it’s lost. If you have your IMEI number, you can report it to your mobile carrier and law enforcement authorities.
When you report a stolen phone with its IMEI, carriers can blacklist the device, making it unable to connect to cellular networks in your country and often internationally. This doesn’t help you recover the phone directly, but it renders the device useless to thieves, reducing their incentive to keep it.
Some third-party services and law enforcement agencies can track phones by IMEI number through cooperation with carriers. However, this method typically requires police involvement and is generally less effective for quick personal recovery compared to the previous methods. It’s most useful for permanently disabling stolen devices and potentially identifying theft patterns.
Method 4: Specialized Tracking Applications
The fourth and often most effective method involves dedicated phone tracking and security applications. These specialized apps must be installed on all your devices before any loss occurs, creating a network of connected devices that can locate each other.
Popular tracking applications in 2026 include Prey Anti Theft, Cerberus, Lookout, and various commercial monitoring solutions. These apps typically offer more features than built-in solutions, including photo capture of the thief using the front camera, screenshot capture of their activities, SIM card change alerts, and more aggressive location tracking that works even when standard location services are disabled.
Many of these applications run in stealth mode, making them difficult for thieves to detect and remove. They can survive factory resets in some cases and continue reporting the phone’s location even after significant tampering. Some advanced versions can even record ambient audio, track WhatsApp and other messaging apps, and provide detailed activity logs.
Family tracking apps like Life360, Family Locator, and carrier-provided services also fall into this category. While primarily designed for keeping tabs on family members’ locations for safety, they become invaluable for device recovery when needed.
Combining Methods for Maximum Effectiveness
The most effective approach to phone security involves using multiple tracking methods simultaneously. Install both the built-in tracking service for your operating system and at least one third-party tracking app. Keep your IMEI number documented in a safe place separate from your phone. This layered approach ensures that if one method fails or is circumvented, you have backup options for locating and securing your device.
Regular backups to cloud services like iCloud, Google Drive, or dedicated backup solutions ensure that even if you can’t recover your physical device, you won’t lose your photos, contacts, documents, and other irreplaceable data. In 2026, most services offer automatic daily backups that require no user intervention once configured.
Prevention remains the best strategy. Use strong biometric security like facial recognition or fingerprint scanning combined with a complex password. Enable automatic locking with a short timeout. Consider a phone case with a wrist strap or lanyard for situations where loss is more likely. Keep your phone’s software updated, as security patches often address vulnerabilities that thieves exploit.
Understanding these phone tracking methods and implementing them proactively transforms the stressful experience of losing your phone from a complete disaster into a manageable inconvenience. With the right preparation and quick action, you significantly increase your chances of recovering your device and protecting your valuable personal data from unauthorized access.